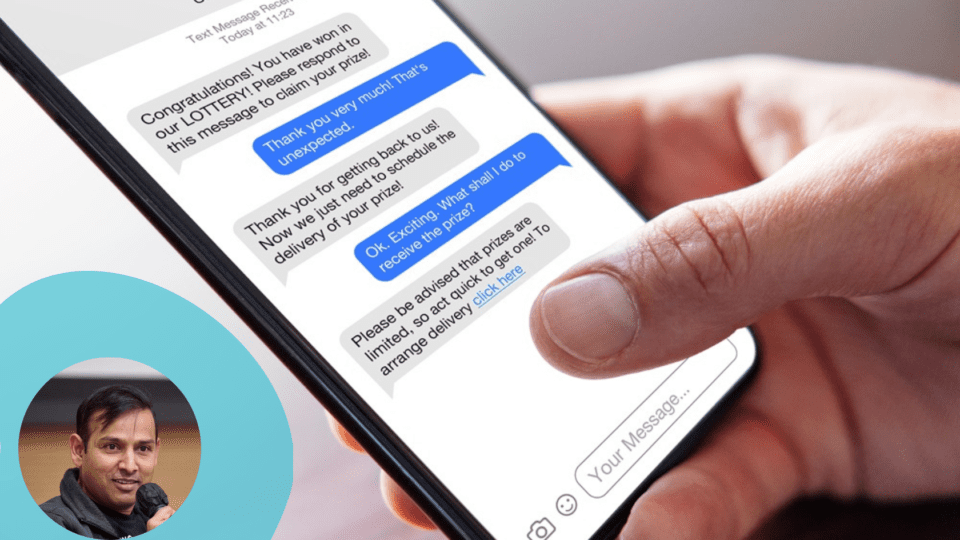
Cybercriminals are increasingly employing social engineering tactics to catch people when they’re exercising what psychologist Daniel Kahneman calls “System 1” thinking: A mode of cognitive processing characterized by making quick decisions and judgments based on patterns and experiences.
Many of us have shared the following experience: You’re going about your day when you receive a text saying your package from Amazon couldn’t be delivered and you need to log into your account to resolve the issue. The thoughts that cross your mind in response could range from, “I’d better get this handled,” to “Wait, did I even order anything from Amazon?” to “Hold on, is this legit?”
In a perfect world, we would all pause to question the validity of the text message. But for many of us, ecommerce is so deeply engrained in our lives that it’s not uncommon to receive packages we don’t even remember ordering. Socially engineered attacks are particularly effective during peak shopping seasons, when consumers are even more busy and relying on “System 1” thinking, but consumers and retailers alike must stay vigilant year-round.
This is especially pertinent as bad actors increasingly leverage artificial intelligence (AI) to carry out more sophisticated attacks at a higher volume. One study found that IT leaders have observed AI-backed phishing attacks increase 51%. Additionally, the FBI recently issued a warning that cybercriminals are using generative AI to make the language in their attacks more convincing by eliminating some of the telltale signs of a scam, like spelling and grammatical errors.
Below, we’ll explore the cognitive biases that make socially engineered attacks successful, followed by strategies consumers and retail application developers can use to enhance security.
The 5 Biases Behind Social Engineering
1. The halo effect.
The halo effect refers to people’s tendency to trust brands they have a positive impression of. 29% of phishing attacks exploit this bias by posing as a trusted entity to lure in unsuspecting consumers. A notable example of this is the American Express email phishing scam that tricked cardholders into opening a malicious email attachment to gain access to their accounts.
2. Hyperbolic discounting.
Hyperbolic discounting refers to humans’ preference for smaller, immediate rewards over larger, delayed rewards, which is what makes discounts so irresistible. Cybercriminals exploit this bias by creating fictitious deals, like when scammers launched a series of phishing campaigns to steal consumer data under the guise of shopping deals.
3. The curiosity effect.
Cybercriminals take advantage of consumers’ curiosity by presenting them with information that piques their interest in an effort to get them to divulge their private information, like the fake delivery notice phishing scams discussed previously.
4. The recency effect.
The recency effect refers to people’s tendency to focus their attention on urgent or recent matters. Cybercriminals have capitalized on this bias by sending out fake Box notifications alerting users that someone is trying to share a file with them, compelling them to take immediate action.
5. Authority bias.
Authority bias taps into people’s tendency to attribute credibility and validity to entities they perceive to be in a position of authority. Bad actors have been known to distribute phishing emails impersonating organizations such as the U.S. Supreme Court, or even peoples’ bosses.
Shopping Smart: How Consumers can Avoid Socially Engineered Scams
Being cognizant of the biases above is critical to avoid falling prey to socially engineered scams. These attacks rely on “System 1” thinking, so carefully reading emails and text messages, double-checking that URLs are legitimate and pausing to think before sharing personal information goes a long way in avoiding these attacks.
Consumers should also enable multi-factor authentication (MFA) and opt for strong authentication methods, ideally those that are passwordless (more on this shortly), whenever available. Additionally, as AI-powered attacks become more common, consumers need to educate themselves on what these types of scams look like, whether it’s advanced phishing emails or hyper-personalized spear phishing attacks.
The Application Developer’s Role in Bolstering Security
When it comes to preventing socially engineered attacks, much of the responsibility lies in the hands of retail app developers. It’s up to them to set consumers up for success by providing robust authentication methods that are easy for users to opt into and use.
Passkeys are a user-friendly, phishing-resistant authentication method that eliminates the need for passwords by verifying a user’s identity via cryptographic key pairs. In fact, testing conducted by Google revealed that passkeys have a 50% higher success rate and enable logins twice as fast as password-based systems. In addition to providing better security, passkeys also improve the user experience (UX) by reducing friction, which is why the world’s largest online retailer, Amazon, has implemented them.
Providing MFA options is another way retail app developers can secure consumer information. Magic links, for example, let users further verify their identity by simply clicking a unique, time-sensitive URL. For an added layer of security, app developers also can enact step-up authentication as part of their MFA strategy, requiring extra verification before sensitive actions like high-value cart transactions. Both passkeys and magic links make it significantly more difficult for attackers to access consumers’ accounts, even if they’ve already successfully phished their passwords.
Socially engineered attacks in retail aren’t going anywhere. They take advantage of the very cognitive biases that make us human, and that’s precisely why they’re so effective. These scams will only become more frequent and successful as cybercriminals increasingly leverage AI to carry out their digital assaults.
To thwart these attacks, consumers must be aware of their inherent biases and take every precaution they can to protect themselves, and it’s up to retail app developers to provide them with ultra-secure and user-friendly authentication and MFA methods to do so. Adopting the strategies above is a win for everyone: consumers benefit from a more secure, seamless shopping experience, and retailers drive more sales by fostering trust and convenience.
Rishi Bhargava is Co-founder at Descope, a developer-first authentication and user management platform. In a career spanning over 20 years, Bhargava has run product, strategy, go-to-market and engineering for category-creating cybersecurity startups and large enterprises. Before Descope, he served as VP of Product Strategy at Palo Alto Networks, which he joined via the acquisition of Demisto. Bhargava was a co-founder at Demisto where the company pioneered the “security orchestration” category before being acquired. Prior to Demisto, he was VP and GM of the Datacenter Group at Intel Security and launched multiple products at McAfee (acquired by Intel).