Every day, more brands fall victim to industrialized counterfeiting. According to the United Nations Commission on Crime Prevention and Criminal Justice, counterfeiting is now the second-largest source of criminal income worldwide. Significantly, it has also been linked to the financing of terrorist activities, offering a lucrative and relatively low-risk source of funds.
While counterfeiting is a growing concern for law enforcement agencies, it is brands that suffer most in terms of lost revenue and diminished reputation. The relentless digitization of commerce has amplified the effectiveness of counterfeiters by offering new online avenues of opportunity to push their fake products and new ways to imitate brand owners.
Sophisticated counterfeits sold online, or even in legitimate channels, are hard to spot. In the case of Apple, hundreds of imitation iPhones, all with apparently legitimate serial numbers, managed to evade US Apple store staff, costing the company more than $6 million. Over the past several years, counterfeiters have also taken to social media to peddle their fake wares.
In 2019, GhostData found that 56,000 Instagram accounts were associated with the counterfeit of luxury brands, representing a 171% increase since 2016. These accounts generated 64 million posts to promote imitation products, up more than 300% from 2016. Transient content, such as Instagram Stories, make it easier to trade fakes while leaving fraudulent digital footprints.
Fighting Back Against Fakes
In 2021, U.S. Customs and Border Control seized 27,000 shipments containing counterfeits worth an estimated $3.3 billion. Earlier this year, a raid by French customs found enough fake Louis Vuitton fabric to cover 54 tennis courts.
But brand owners know that even the most sizable seizures and the committed efforts of government agencies still leaves them with a systemic problem that is getting worse. Brands already deploy a variety of techniques, including product authenticators for consumers and inspectors, supply chain monitoring and consumer education. But the brand response must also mirror the proven techniques of intelligence-led law enforcement. By combining expert analysis and investigators with technology, targeted interventions become possible.
From Online Brand Protection to Intelligence-Led Enforcement
Conventional brand protection strategies can help brand owners take down a steady stream of online counterfeits and even individual counterfeit networks. But the most persistent and organized adversaries will be operating at a different scale entirely and, even after countless enforcement notices, brands may struggle to deter repeat offenders who may already be operating or opening new routes to consumers. So how to go about tackling this problem?
As in law enforcement, the answer is a systematic, multi-disciplinary approach, combining enterprise-scale open-source intelligence gathering with expert analysis and investigation. So while technology and data provide part of the answer, interpretation of information, as well as physical sources, yields valuable insights and evidence for brand owners. This means a critical role for analysts that bring context and experience, for field investigators that dig into the roots of counterfeit operations, and for case managers that prepare evidence.
Connecting the Dots to Find the Most Serious Counterfeiters
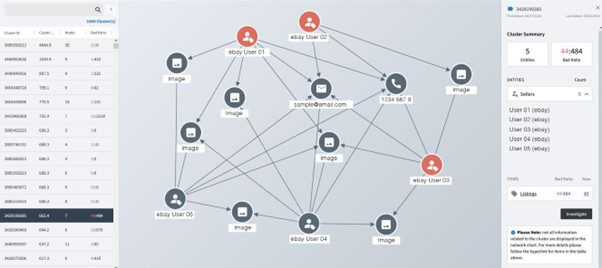
Tackling systemic, sophisticated offenders starts with uncovering their networks. This requires a technique known as clustering to connect and analyze data points from multiple online channels and identify common threads between counterfeit networks and accounts. Once an account has been singled out, its IP and email addresses, phone numbers and URLs provide a means to connect them to other similarly suspicious accounts.
Analytical tools then provide a cluster score to prioritize listings for further investigation. When viewing a cluster, an analyst can calculate the number and types of links between multiple online accounts. The entities could include website registrants, marketplace sellers and social media profiles.
Analysts link clusters to form secondary and tertiary networks and establish high-value targets. These refer to the infringers that are benefitting the most financially from nefarious activity. By inspecting a cluster with multiple counterfeit data points, brands can discover other potential infringers. For example, in the cluster below, three websites identified as counterfeit share the same email address and domain administrator. The same email address is used by another website, not yet identified as a counterfeit seller. Since the unflagged website shares the same phone number as the two counterfeit websites, we can surmise that this website also belongs to an infringer and investigate accordingly.
Bringing Human Expertise into Intelligence-Led Investigations
Combining data from these tools with custom research, investigators can gather actionable intelligence and begin to build a dossier. For example, an investigator may find a product listed for sale online at a price below MSRP. Listings may have product images that show an altered logo, inaccurate product descriptions or a seller location that does not match a brand’s location. This is the start of the evidence that can be used for litigation. Investigative techniques can then be used to infiltrate groups and take down the worst offenders.
Investigators can adopt covert aliases that are used to conduct test purchases of products, which can be shipped to a secure evidence location. This allows communications with the sellers to be documented and used as evidence. Photographic and video data can link production sites with illegal activity that is often on an industrial scale.
Once investigators have gathered sufficient actionable intelligence and evidence, they work with law enforcement to shut down operations and equip the brand owner’s legal team to pursue civil action. The expert work of investigators, often bringing experience from law enforcement careers, drives successful legal outcomes and eliminates criminal networks, as demonstrated by the many civil cases and federal proceedings underway currently.
Partnerships are the Basis for Tackling the Scourge of Counterfeiting
Leading brands work with specialist brand protection services to bring more sophisticated, systematic methods to their anti-counterfeiting efforts. They recognize the role that technology is increasingly playing, but only in conjunction with the insight and expertise of experienced analysts and investigators. Strong partnerships between law enforcement and the commercial sector are essential. But a more strategic model for brand owners and their brand protection providers can also deliver superior results, with enduring relationships the basis to cultivate an understanding of product ranges and related counterfeit hotspots.
For brands looking to better understand their options, bodies such as the International Anti-Counterfeiting Coalition (IACC), which promotes collaboration amongst leading brands and brand protection players, offer a focal point and resource. OpSec Security is one such IACC member that has combined technology and human expertise, as well as building enduring long-term relationships with its customers. But whichever provider a brand opts for, it needs to ensure that its valuable, vulnerable brands are protected with an intelligence-led response that is as adaptable and sophisticated as the counterfeiters themselves.
Stuart Chaffin is Senior Director, Investigative Services at OpSec Security. A certified criminal and civil investigator, Chaffin has a proven track record for security management, asset protection, investigation leadership and law enforcement operations management, both nationally and internationally. His career spans 30 years working in law enforcement, security and investigative services. Chaffin developed and managed a global enforcement program, working with key governmental partners including the FBI, Homeland Security, foreign law enforcement agencies and others to investigate brand enforcement and IP infringements. Chaffin also served as a Cross-Designated Taskforce Special Agent for the Department of Homeland Security and the Department of Justice and is a certified cybersecurity professional.




